A Verifiable Approach to Network Switch Sanitization
When Dynamic Lifecycle Innovations conducted a forensic study of network switches sold on the secondary market as “sanitized,” the results revealed an important lesson for the industry. Despite documented deletion efforts, recoverable configuration data, including IP and MAC address references and DHCP records, remained on one of the tested devices. This study, validated through independent analysis by CPR Tools, underscored a critical reality: effective data destruction on network equipment requires more than basic deletion commands or factory resets. It demands a verifiable, structured process designed to address how data actually persists on network hardware.
Why Process Matters for Data Sanitization
As network switches reach end–of–life, organizations face a critical responsibility: ensuring all data has been securely and completely removed before equipment is reused or resold. While many sanitization methods rely on basic console to delete commands or factory resets, these approaches often fail to address how data actually persists on network hardware.
Dynamic’s Sanitization Process and Proven Results
To close this gap, Dynamic Lifecycle Innovations developed a multi-stage, software-guided sanitization process designed to deliver verifiable data security for network switches and other enterprise networking equipment.
Step 1: Intelligent Device Profiling
Effective sanitization begins with understanding the device itself. Dynamic’s process first probes the device firmware to identify make, model, serial number, and OS/firmware version. This ensures the correct recipe, accounting for platform-specific storage behaviors and erase capabilities.
Step 2: Credential Clearing and Access Enablement
Configuration files are removed early in the process to eliminate stored credentials and legacy passwords. This step ensures full administrative access for subsequent sanitization actions and prevents inherited access risks from persisting on the device.
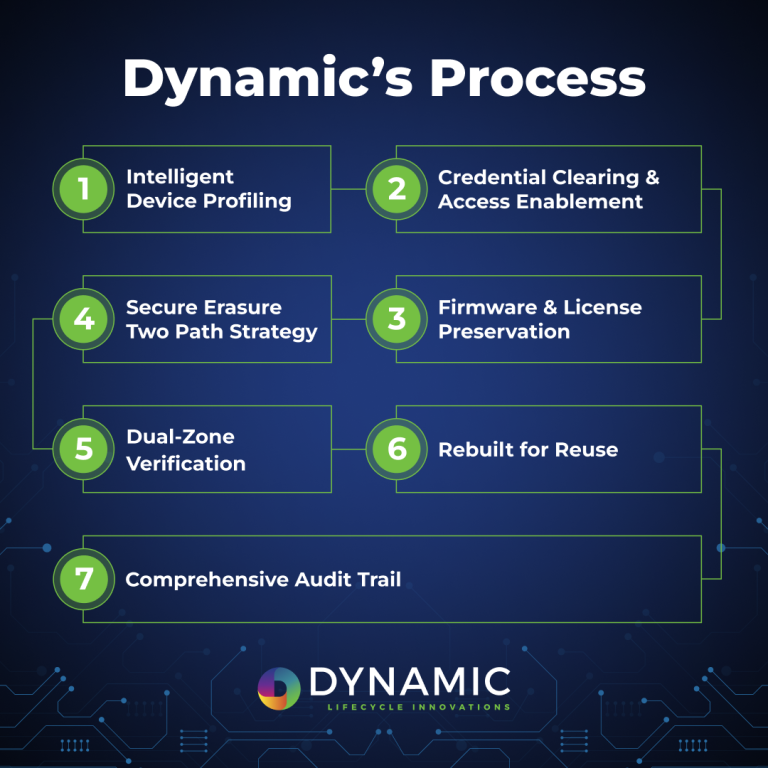
Step 3: Firmware and License Preservation
Before erasure begins, a clean, stock copy of the operating system image and any embedded licenses are securely extracted and stored off-device. This preserves legitimate value for downstream buyers, while ensuring that no customer data is retained.
Step 4: Secure Erasure Using a Two-Path Method
Dynamic executes firmware-native secure erase commands whenever the platform supports them. If native commands are not supported, the process falls back to a validated overwrite of all Flash storage.
Step 5: Dual-Zone Verification
The process performs read-back verification of both Flash and NVRAM to confirm that all storage zones have been properly overwritten or cryptographically purged. This step validates the data sanitization with evidence.
Step 6: Rebuild for Reuse
After verification, the original firmware image and licenses are restored. The device is reinitialized to a default state and prepared for safe aftermarket deployment, supporting circular IT practices without compromising data security.
Step 7: Comprehensive Audit Trail
Every action, hash check, and verification step is logged and tied to the asset’s unique identifier. This creates a defensible chain-of-custody record that supports compliance, audits, and internal governance.
Network switch sanitization should be provable, repeatable, and auditable.
To see how this process performs under forensic scrutiny and why it matters, read the full Network Switch white paper.
Related Resources










